How secure is .rs?
In 2014, we did a report titled “National domain security analysis” (pdf) under RNIDS (Serbian National Internet Domain Registry) sponsorship. This study was then presented (same year) on debate panel “3u1” during “European Cyber Security Month”, organised by ENISA, the European Union Agency for Network and Information Security and RNIDS.
Participants, general public and media showed broad interest in this study and it was well received by media at that time. Blic, B92, Live TV, IT Svet, PC Press, Biznis i Finansije, Personal Mag, Dnevnik, etc.
This resulted in more panels, presentations and improvements over original report, mainly at ETF (Faculty of Electrical Engineering), FON (Faculty of Organizational Sciences), Faculty of Security Studies and others.



Our hope was that this 2014 report and analysis will serve as foundation for business and technical decision makers. As the security threat increases and privacy concerns heighten, the relevancy and timeliness of this report is significant, underscoring the imperative that data security, protection and privacy need to be integrated into every service, business process, web site and mobile application.
2014 report and analysis (pdf) #
This study covered 86.291 national internet domains (.rs)
Covered points:
- Domain DNS settings
- Domain MX settings with active check for smtp/imap/pop3 services
- Domain active web services (http and https)
- Geo IP location for domain services
- OS/Version check for web/mail services
- Detailed analysis of web service encryption protocols and settings including HSTS.
- Detailed analysis of mail service encryption protocols and settings
Serbia on the Internet in 2014:
- 2.85 million Internet users in Serbia
- 1.3 million that use e-services
- 99% companies in Serbia uses Internet
- 28.3 million dinars (235k EUR) spent each day in Serbia on buying/selling items over Internet.
Results of this analysis where not encouraging to say at least. Out of 79.1% domains that had web service active, only 54.3% had HTTPS enabled, and out of them only 14.2% had HTTPS set correctly. On the mail transport side, out of 81.9% of domains that had SMTP service active, 49.1% supported encryption and out of them only 13.5% had it set correctly.
On top of that:
- Out of Top20 web sites in Serbia, only one site had HTTPS enabled for visitors.
- Out of 40 official internet domain registers, 13 of them had valid CA signed SSL certificate and 1 (one) had HSTS active.
- In total, only TWO domains out of 86.291 had HSTS active (that is 0.002%).
HTTPS & usage of HSTS #
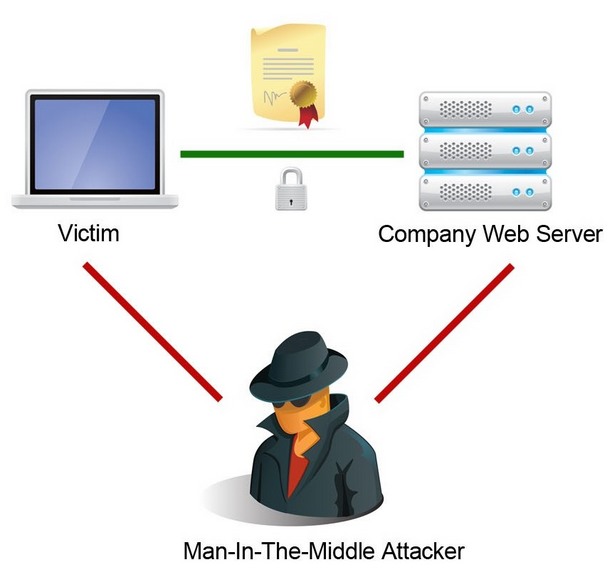
During our panels, discussions, interviews and training’s we explained dangers of encryption miss-configuration, usage of obsolete encryption standards and protocols. One of major points was explaining that (HSTS) should be enabled for all web encryption setups. In a 2009 paper, Moxie Marlinspike introduced the concept of SSL stripping, a man-in-the-middle attack in which a network attacker could prevent a web browser from upgrading to an SSL connection in a subtle way that would likely go unnoticed by a user.
The HTTP Strict Transport Security (HSTS) specification was subsequently developed, drafted in 2010, and accepted in 2012 as RFC to combat these attacks. Since 2012 all major banks, retail companies, etc. in world (except in under-developed countries - including Serbia) adopted this technology and implemented it to combat MiTM attacks. The major reason for us to push HSTS during our presentations and conversations, was discovery that only 0.002% of all national domains in Serbia used it.
Privacy on the Internet #
Second major point was also trying to engage audience about need, to have privacy on the Internet. The one most common statement among students at that point was: “We don’t care about rights to privacy, because we have nothing to hide”. For perfect answer, we can quote (Edward Snowden): “This is not different than saying: We don’t care about freedom of speech because we have nothing to say”.
2016 addition to the report: e-Banking in Serbia #
In 2016 we analyzed how banks in Serbia protect users with encryption during web access, to see how well users are protected. The criteria used in this addition is highly relevant to the security and privacy practices banks must implement to maximize online trust and consumer protection in e-banking.
This analysis include:
- Detailed analysis of web service encryption protocols and settings including HSTS.
- Encryption policy before POST
- Provider for delivering e-Banking service (in-house and/or outsourced)
This analysis does NOT include:
- Application level security
- Bank procedures for using e-banking web applications
- 2FA implementation security
Like in our 2014 results for overall national domain security, new survey and analysis results are not encouraging to say at least. To some extent we can safely say that they are frightening.
The e-Banking preliminary summary #
Out of 22 Banks & 29 sites analyzed, 0 (zero) use HSTS.
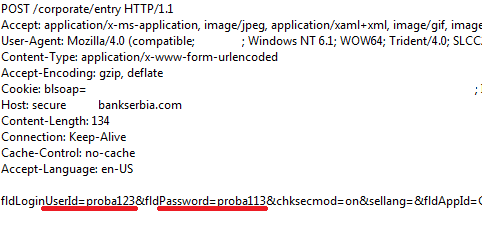
Out of 29 e-banking sites only 4 (four) e-Banking sites encrypt passwords before POST. Rest, use pure plaintext mode relying on HTTPS protection without HSTS! Example:
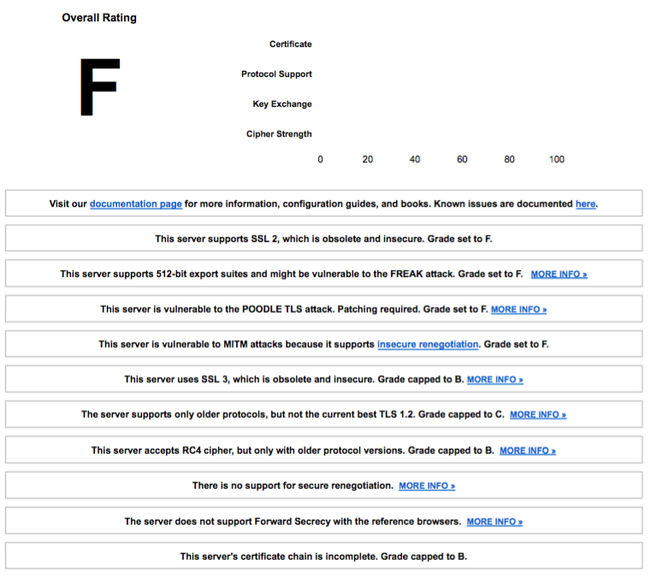
- Out of 29 e-banking sites 9 (nine) have F grade in security (worst possible grade) checked on Qualys (The leading provider of Information Security and compliance cloud solutions). SSL test web site and results are bellow saved for reference. F grade is mostly due usage of self-signed certificates, unsafe (obsolete protocols/encryption standards, and/or due to known vulnerabilities enabled/used). Here is one of examples summary:
Out of 29 e-banking sites 11 (or 37.93%) use outsourcing services (Pexim/Asseco or Halcom). All of which use same SSL/TLS certificate signed by outsourced company and not Bank(s), completely relying on HTTPS with passing of plaintext passwords, and again not using HSTS. Also Banks “trust” these third parties with customer data, most likely without notifying customers about where that data is, and who has access to it.
Some support 2FA (Two Factor Authentication) that is enabled with either mobile phone application, or sms, or other means (tokens, etc) but almost all of them use 2FA only for payment and not for login (accessing your data). This practically means that someone with MiTM capabilities is likely to get access to your private account and get full insight on your financial information.
Conclusion #
With above mentioned failures to meet the best practices securing data in transit, I will leave any comments to the reader. Mine would not be appropriate after observing above mentioned failures.
It might be worth mentioning that EU HQ’s of some Serbian banks have all these security features implemented correctly, while in Serbia they do not. Maybe, if this was regulated by local Serbian law, and if that law would implemented in such way to protect consumers, banks would take care to implement best possible standards to protect it’s customers. Unfortunately, majority will continue to pay “Account maintenance fee” on monthly basis and accept the conditions.
If you liked this, I would highly recommend you to also read “E-banking: Defective by design” by Dušan Dželebdžić i Žarko Ptiček
UPDATE 2016/01/11: This blog entry was kindly translated to Serbian: Koliko je naš e-banking zaista siguran? and published by Netokracija.rs
UPDATE 2016/01/14: Another blog showed up (not related to our work), mostly same topic different domains on Serbian “Zašto se browseri plaše sajtova državne uprave?”
UPDATE 2016/01/15: Looks like this is not only in Under-developed countries, as Brian X. Chen @bxchen - Lead consumer technology writer and author of the Tech Fix column for @nytimes sent unrelated tweet on almost same topic noticing “World of Warcraft has better password security (2-step verification) than some banks (e.g. Capital One). That’s nuts.” in his tweet published here.
UPDATE 2016/01/22:
First bank that officially responded to this report was Societe Generale Serbia. Public statement was published here and here. This was not surprising since this is one of the banks that actually took all but HSTS measures and had A- in report.
UPDATE 2016/03/07:
Second bank to respond and correct issues mentioned in above survey was UniCredit Bank.